Basic Concepts and Functions of Access Token
In modern web applications, the access token is widely used for authentication and authorization purposes.
For user login sessions, the server generates a login token after verifying the user's identity. This token is used to maintain the user's login state and prove their identity in subsequent requests. Additionally, in scenarios where API access is required, such as GitHub services, users can generate a token to access API. These tokens are generated when the user is logged in and authorized, allowing users or third-party applications to access specific API resources without a complete login process every time.
These two token mechanisms enable flexible and secure identity verification and access control, significantly enhancing user experience and system security.
Overview of API7 Enterprise's Feature: Token Management
The token management feature provided by API7 Enterprise enables administrators to easily generate, edit, delete, and regenerate tokens.
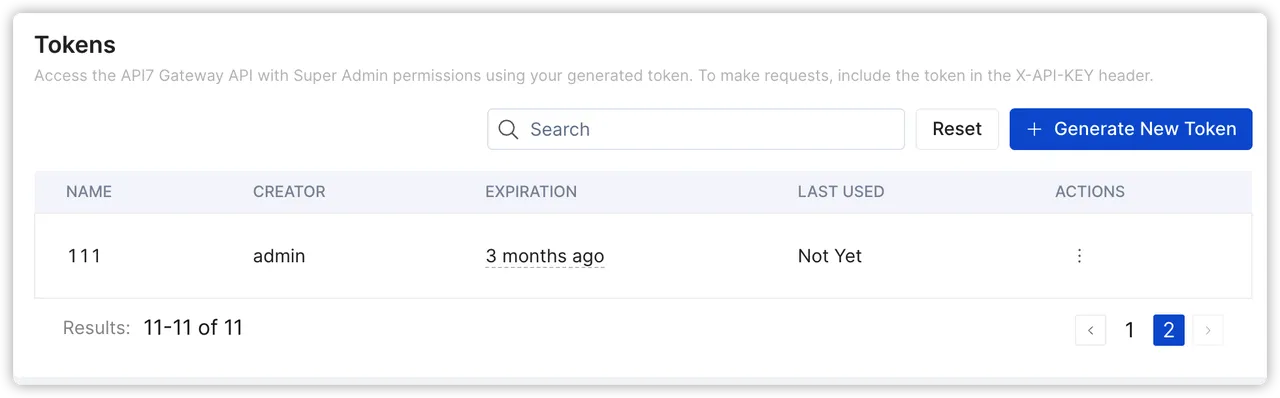
Generating Token
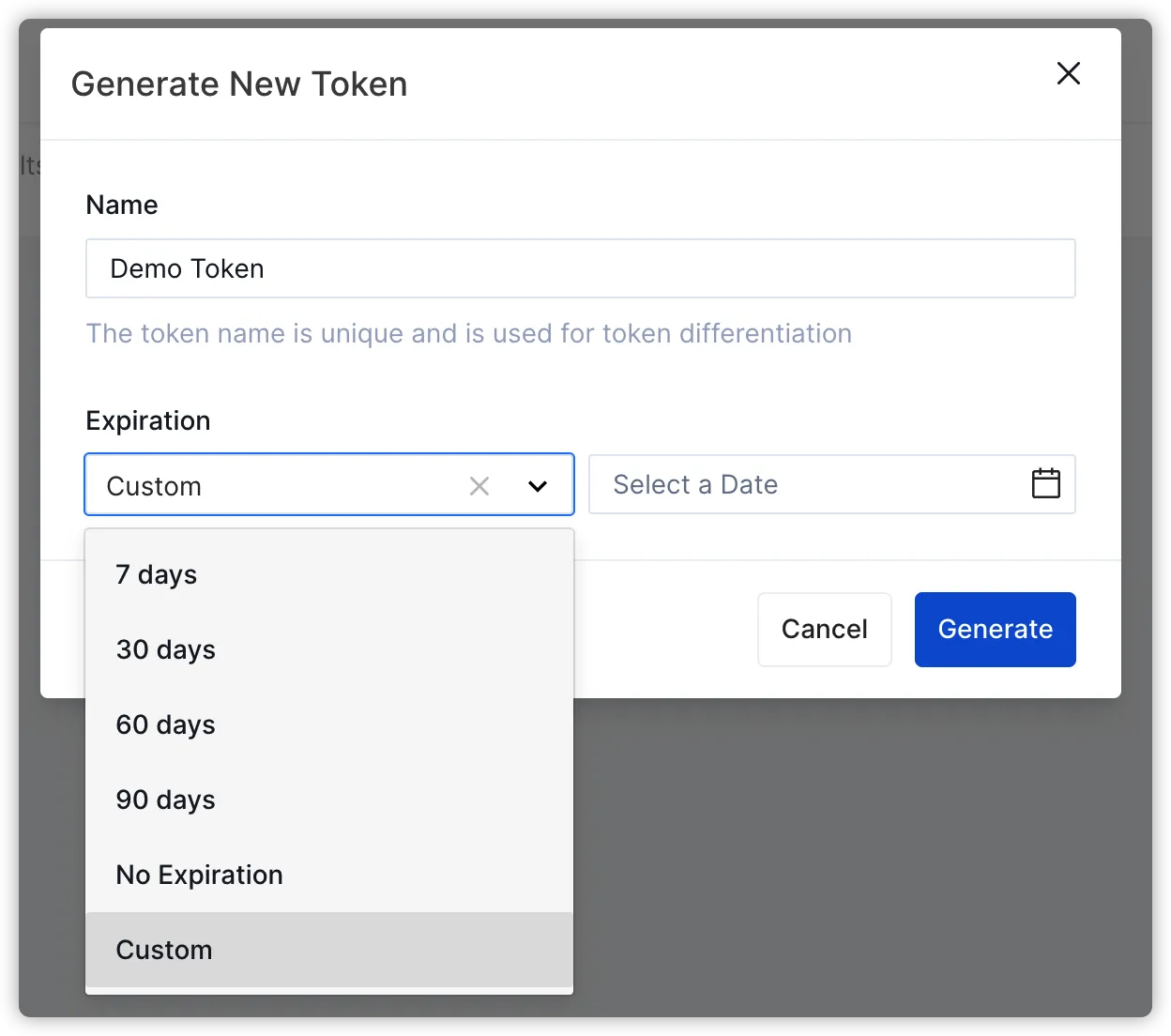
Administrators can generate new tokens through simple operations in the management interface of API7 Enterprise. During the generation process, the token's name and expiration time need to be specified.
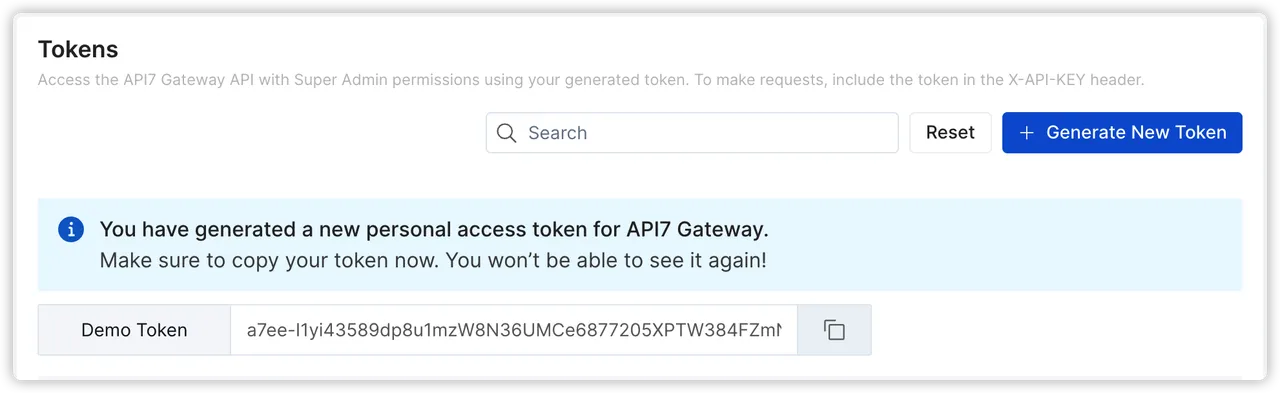
Once generated, the specific value of the token will be clearly displayed at the top of the list for quick reference. To ensure security, the token value is not fully displayed but requires horizontal scrolling for viewing. Users can copy the token value to the clipboard for later use by clicking the copy button. It's important to note that the token value is displayed only once after generation on this page. Once you leave the current page, you won't be able to view the token value within this platform again. Therefore, it's crucial to securely manage your token to prevent unauthorized access.
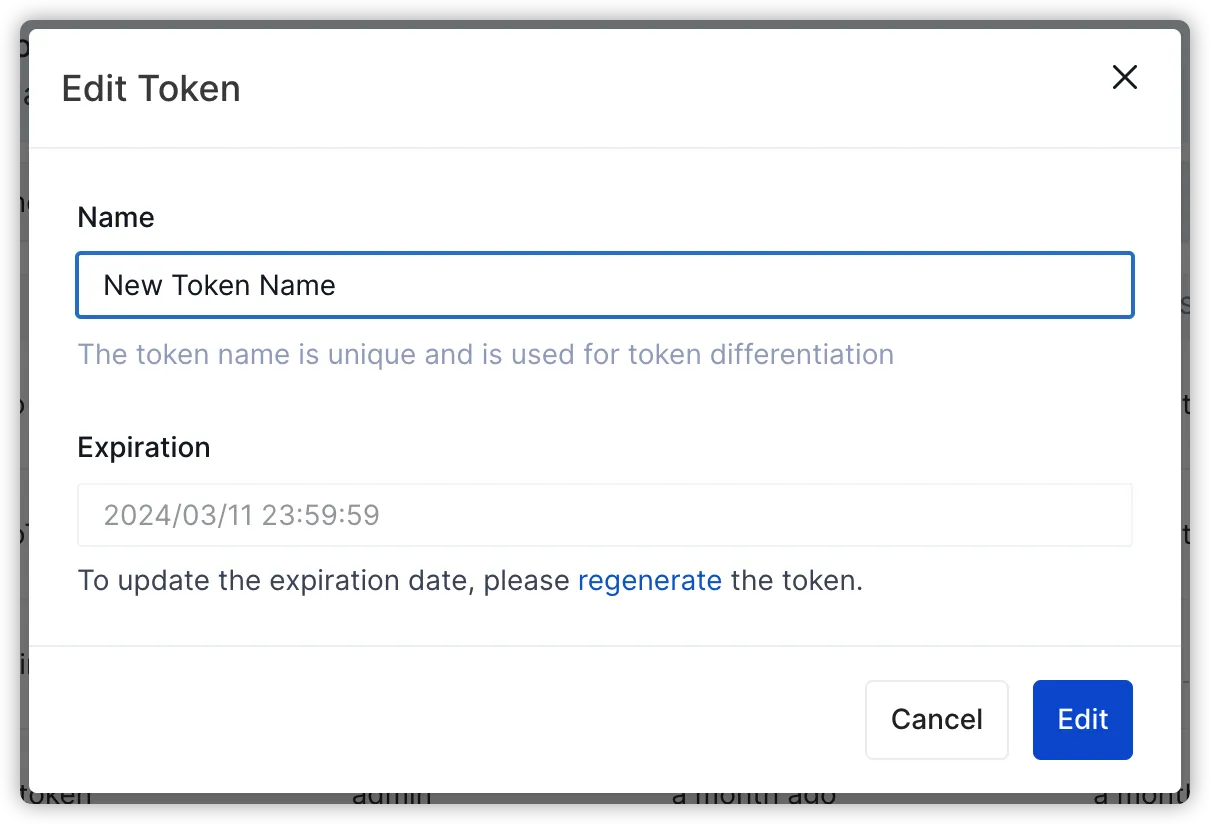
Editing Token
This feature allows administrators to modify the name of existing tokens. However, it's important to note that editing a token itself does not directly affect the validity or behavior of the token in use. It's solely used for optimizing token identification and differentiation, facilitating management and usage.
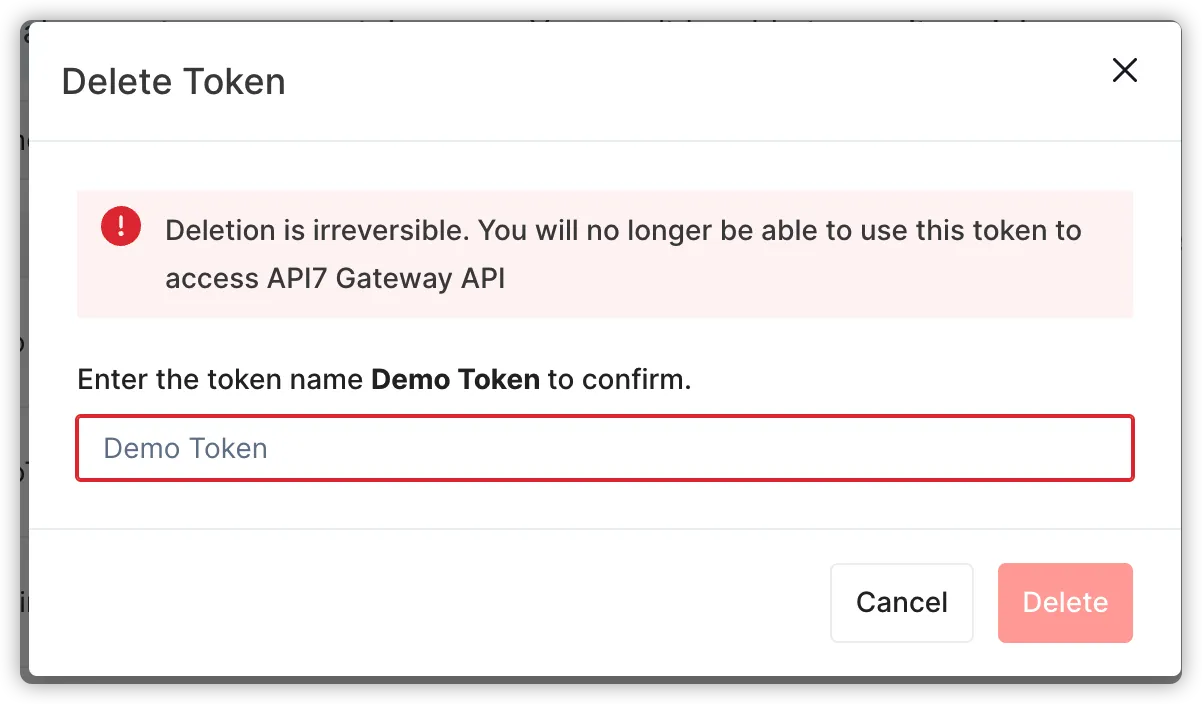
Deleting Token
When a token is no longer needed, administrators should delete it to reduce security risks. The deletion operation is irreversible, and once executed, all accesses related to that token will immediately terminate.
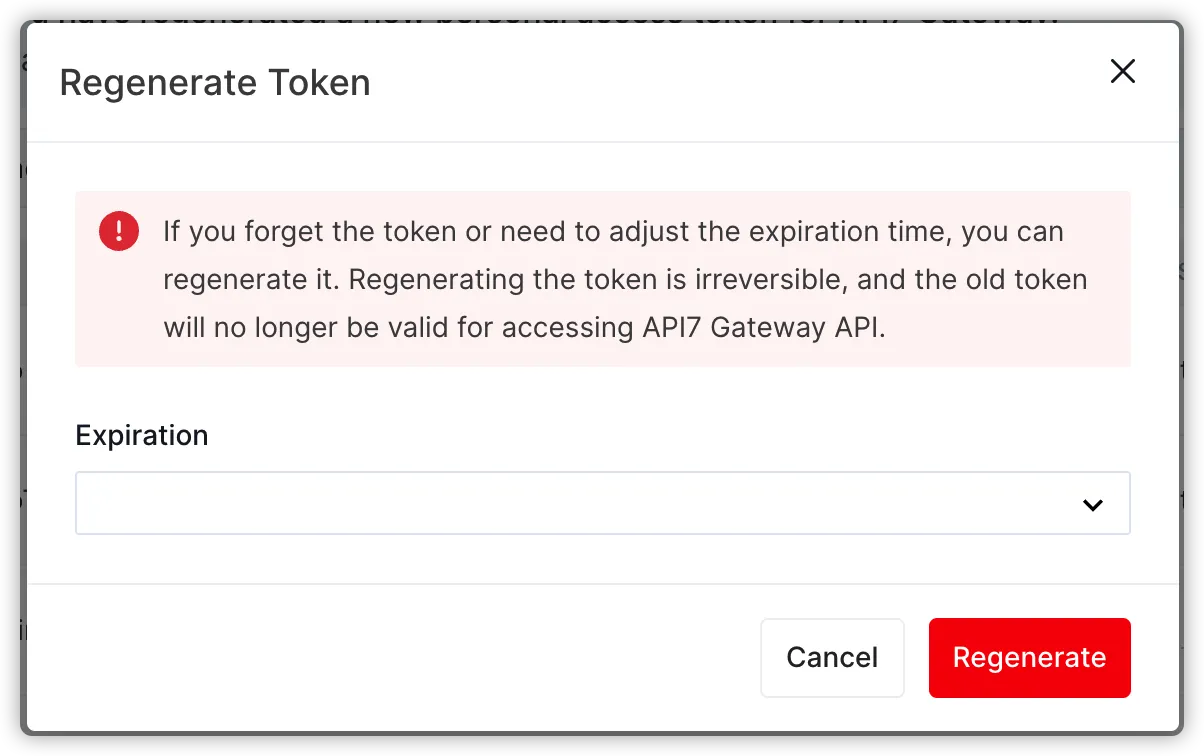
Regenerating Token
Regenerating a token is a necessary operation in certain situations, such as suspected token leakage. The regeneration function creates a new token while invalidating the old token.
When to Use Token?
Upon receiving the token, the client needs to include it in the HTTP header X-API-KEY for each request sent to API7 Enterprise's API to allow the server to verify its identity and authorization.
Token Security Management
Expiration Policy
Properly setting the expiration time of tokens not only effectively reduces potential risks caused by token leakage but also ensures the overall security of the system. To achieve this goal, administrators need to carefully balance business requirements with security considerations.
Setting a short expiration time for tokens can significantly reduce the attack window. Even if a token is inadvertently leaked, attackers can only exploit it for a limited time. However, too short an expiration time may increase the frequency of user logins, negatively impacting user experience. Therefore, administrators need to set an appropriate expiration time based on the actual usage of the system and its risk tolerance.
Additionally, administrators should regularly review and update the token expiration policy. As business evolves and the external threat landscape changes, the originally set expiration time may no longer be applicable. By regularly assessing and adjusting the policy, the system's security can be ensured to remain optimal.
Access Logs and Auditing
To monitor token usage and promptly detect abnormal behavior, API7 Enterprise logs all accesses and operations related to tokens. These logs provide detailed records of token generation, usage, modification, deletion, and other operations, including timestamps and user information. They serve as crucial evidence for security auditing and troubleshooting. By regularly reviewing and analyzing these logs, potential security threats can be promptly identified and addressed. Moreover, these logs are essential sources of information for tracing the origins of issues and recovering data. In the event of security incidents or data loss, these logs can be leveraged to quickly pinpoint problems and take remedial measures.
Conclusion
With the widespread adoption of cloud computing and microservices, API security issues are becoming increasingly prominent. As one of the core mechanisms for authentication and authorization, the management and security of tokens are crucial for protecting API access and data transmission.
API7 Enterprise provides users with a reliable and user-friendly API security solution by offering comprehensive and flexible token management features along with robust security measures. In the future, as technology advances and application scenarios expand, API7 Enterprise will continue to enhance the security and usability of token management, providing users with more high-quality and efficient services.
